SaaS applications can be accessed by anyone with an internet connection. This introduces many benefits over traditional software such as lower costs, increased scalability, and more flexibility. However, as with any other software, SaaS applications have security weaknesses that we will address in this article. We’ll also discuss what SaaS applications are and some best practices to keep your SaaS applications safe.
What are SaaS applications?
SaaS is an acronym for “Software as a Service”. SaaS applications are web-based software that runs on the cloud. SaaS lets you access programs directly through a browser without having to download and install them onto your computer. It is often cheaper than traditional software because there’s no need for IT teams to purchase, maintain, or upgrade servers needed to host SaaS apps. What’s more, is that they are so easily scalable and flexible than your traditional software because SaaS providers can add or remove servers to accommodate a larger user base whenever required.
What are the security issues in SaaS applications?
SaaS apps are convenient, but they also pose certain security issues. Since they store all user data on remote servers instead of locally on your device, hackers may find it particularly appealing to gain access to all that data under one roof.
If you use SaaS applications for personal reasons (such as email), it is important to protect yourself by using strong passwords and two-factor authentication whenever possible. If you use SaaS apps in your business, make sure employees know how to avoid phishing scams that could lead them into giving away their login details. SaaS apps are also more vulnerable to DDoS (Dedicated Denial of Service) attacks, which can lead SaaS providers to shut down servers.
Assessing the security of your SaaS application:
To start assessing the security of your SaaS application, consider the following factors:
- How sensitive is the data that will be stored in your SaaS?
- What are the potential consequences if this data were to be accessed or stolen by a hacker?
- How easy would it be for a hacker to gain access to the SaaS network or infrastructure?
- What are the current security measures being followed to protect sensitive data?
- How frequently are these security measures updated?
Best Practises for SaaS Security:
It’s difficult to say what makes a SaaS application secure as there are so many different factors. Don’t fret, we have some tips for you that will help keep your SaaS applications safe from common attacks. If you’re a user of SaaS applications, we got you covered too.
Provider end:
- Strong Passwords: Enforce employees to use strong passwords.
- Awareness: Educate employees about phishing scams and how to avoid them.
- Multi-Factor Authentication: Today, most popular services such as Gmail require multi-factor authentication before granting access to sensitive data. Making it compulsory would be a good way to prevent unauthorised access.
- Access Control: Limit access to sensitive data within the company’s chain of command. The most common type of access control in a hierarchical chain of command is RBAC (Role-based access control).
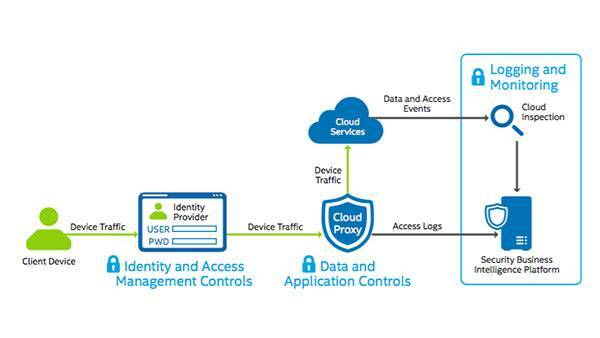
- Network Security: Make sure the traffic between your SaaS app and its servers is encrypted.
- Data Encryption: Ensure data stored by SaaS apps are encrypted with keys that only you have access to in case of an emergency.
- Updates: Keep your software up to date to protect against new vulnerabilities.
- Internal Servers: Use SaaS apps on secure internal servers. If possible, look for providers who offer dedicated private servers to avoid traffic interception problems when communicating between their server infrastructure and yours.
- Testing: Test your SaaS applications for vulnerabilities regularly. Penetration testing is generally preferred. With Apiiro, developers can automatically identify current and future risks from attackers that uses social engineering or other methods to gain access into your system.
- Backups: Back up your data regularly in case of a security breach.
- Disaster Recovery Plan: Have a disaster recovery plan in place. This should include a plan for how you will continue to operate your business in the event of a SaaS security breach.
- External SaaS Security: If IT security audit is not your forte, consider investing in a good SaaS security
User end:
- Strong Passwords: Use strong passwords for your SaaS account and try not to store them.
- Awareness: Know about phishing scams and how to spot one that ends up in your mailbox. Cross-check the URL and look out for “https://”.
- Two-Factor Authentication: If given a choice, pick a provider that uses more than one means of authentication.
- Firewall: No matter what the situation, you want to make sure your firewall is active and updated.
- Anti-virus: Invest in a good Anti-virus, especially if they come with added Internet/Browser Security.
- Software Updates: Most SaaS apps release updates on their server end. Nevertheless, if they have an option to install updates automatically, keep that on! As a general practice, have automatic updates turned on for your device software as well.
- Backups: If the data is very important to you, do keep a backup of it.
Summary
To sum it up, SaaS applications offer several benefits over traditional software, but businesses should be aware of the security risks associated with them. SaaS apps are attractive to hackers because they can be used to steal sensitive information all under one roof. By following the best practices listed above, you can take the first step into protecting your data and keeping your SaaS applications safe from harm. However, if you feel just following these tips won’t be enough do consider investing in a good SaaS security provider.
TechnologyHQ is a platform about business insights, tech, 4IR, digital transformation, AI, Blockchain, Cybersecurity, and social media for businesses.
We manage social media groups with more than 200,000 members with almost 100% engagement.