8 Security by Design Principles for Your Business Solutions – In April 2018, Panera Bread announced that it had a data leak, making 37 million users vulnerable.
Prior to the announcement, Panera Bread had already been warned by a cybersecurity expert that data was leaking from their website.

The American bakery-cafe failed to heed this warning until it was finally forced to take the website down for security maintenance in April 2018.
Panera Bread was just one of the companies that experienced security breaches due to programming oversights. Given the security risks, programmers understand that designing secure applications is a challenging but necessary task.
To significantly reduce risks of successful attacks, these programmers follow specific security by design principles created by the Open Web Application Security Project (OWASP).
These principles ensure that their application is secure down to its foundation. In this post, we’ll be discussing 8 security by design principles that help protect companies from costly cyberattacks.
Let’s get started.
1. Establish Secure Defaults
This principle states that a secure application limits access to resources until access is granted to a user. For a user to gain more access, they have to obtain privileges that give them the option to remove security measures – such as passwords – surrounding those resources.
Applications using this principle prevent unauthorized users from having access to certain resources — making the application secure by default.
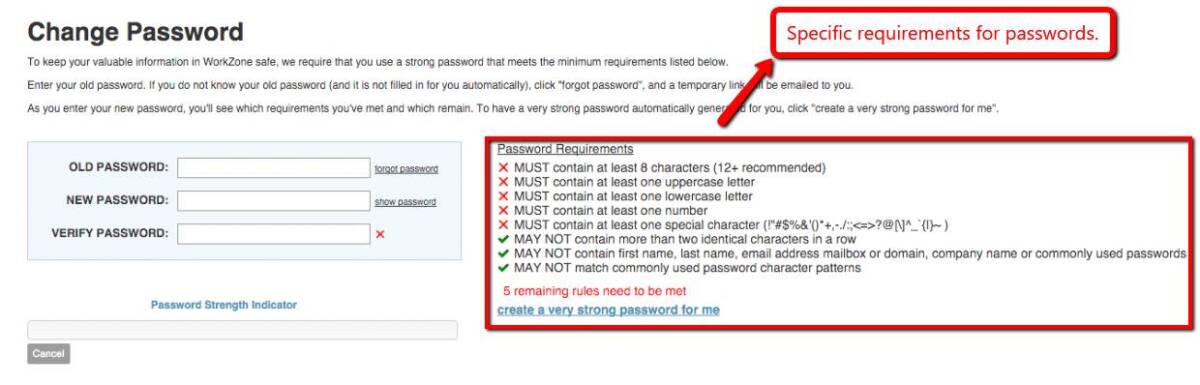
Let’s take Workzone as an example.
Workzone required its users to change and create stronger passwords after their system update. According to Codegrape, a combination of different characters makes it difficult to guess.
Before a user can gain access to the updated website, they must follow specific password requirements.
2. Minimize Attack Surface Area
Every application has features that serve as entry points for security breaches. For every feature added to an application, the attack surface area is expanded, making it more vulnerable to security attacks.
Minimizing the attack surface means that users are restricted from accessing certain areas to reduce entry points for unauthorized users. One way to minimize the attack surface area is to visualize where your vulnerabilities are.
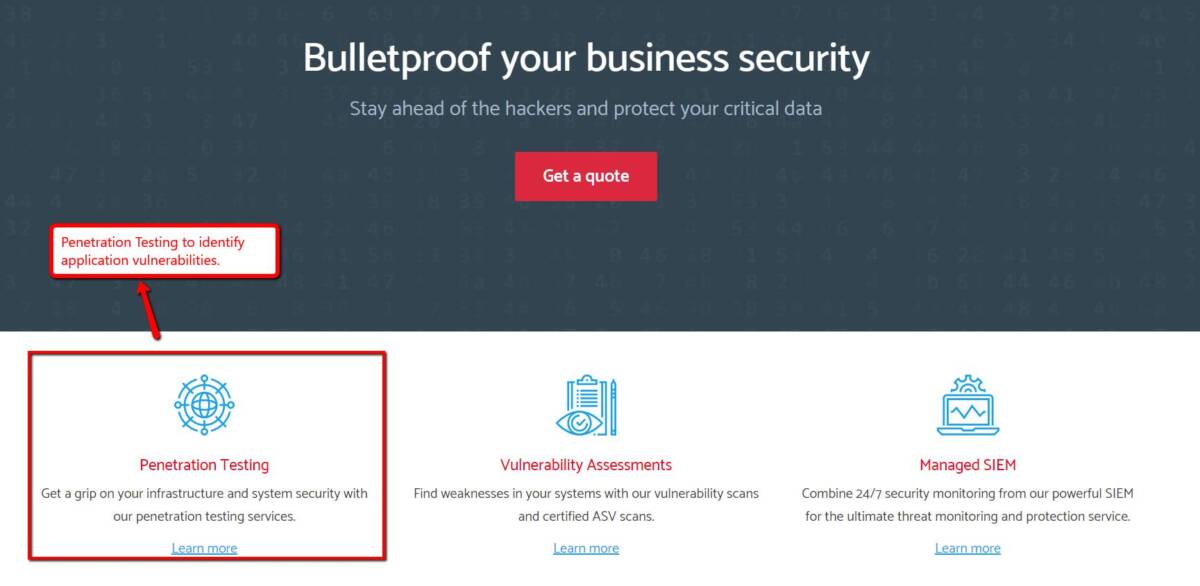
One way to do so is by employing penetration testing to show which areas are weak so they can be corrected and upgraded. When penetration tests are done, you’d be able to determine the security gaps of your network/system, allowing you to address them before you fall prey to the attacks of cyber criminals.
3. Fail Securely
A few applications are prone to failed process transactions every once in a while. Regardless of the reason for failure, sensitive user information and system errors should not be exposed to users.
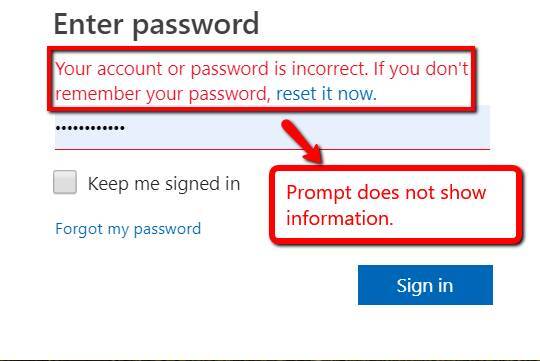
This principle states that only limited information should be shown when errors are encountered by the system. Let’s look at this failed log-in attempt.
The prompt shown did not reveal between which was incorrect between account or password — only the option of resetting the password. Despite a failed log-in attempt, no sensitive information was shown to the user which showed a secure failure.
4. Establish In-Depth Defense
Applications should not rely on just a single security control. The in-depth defense principle states that multiple security controls make attacks less successful due to layers of authorization verifications.
One of the tips given by Open Business Council explains that a single layer of defense is not enough to protect your data from cybercriminals. With multiple layers to secure vulnerabilities, it’s difficult to exploit sensitive information. Cybercriminals will find it less appealing to penetrate.
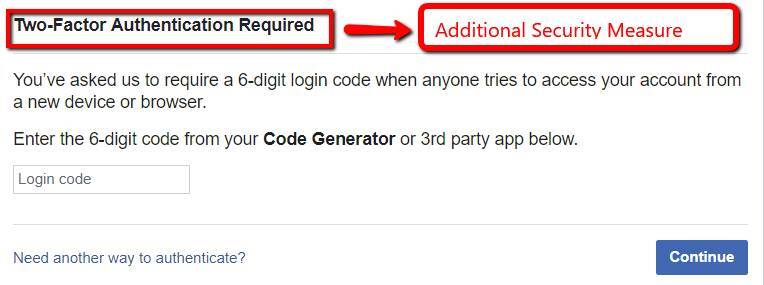
A simple example of this principle is through Facebook user log-ins.
Some applications use a two-step verification process to ensure that the user is the owner of the account.
The application will require the code sent to the phone number of the user before he can enter the application.
5. Separate Privileges
Separation of duties means that individuals must have distinct roles within an application. As an example, let’s use an e-commerce website. On this website, there are administrators and customers.
If an individual is an administrator of the website, he cannot be a customer from its front-end. This is because he might tweak certain administrative tasks that might give him privileges that customers normally don’t have. In this light, customers cannot be promoted as administrators.
This is to prevent fraudulent activities from happening on the application.
6. Lessen Privileges
Generally, users should start with a minimum number of privileges granted to them. These privileges can only allow them to perform their tasks within an application. More often than not, users don’t need additional privileges to perform their tasks. If they need more access, it has to be granted to them by administrators.
Granting them fewer privileges reduces the risk of security breaches from their end. Just like iZooto, they have explicitly stated that their users can request access to certain tasks on their platform before they can perform further tasks.
This is part of their compliance with the new EU regulation, the General Data Protection Regulation. With users classified as controllers who can data and decide what it will be used for, iZooto acts as processors who process data on behalf of their users.
7. Minimize Third-Party Access
For web applications, utilizing the services of third-parties can be convenient for additional functions or data. However, these external parties have different security measures that may or may not be more secure than yours.
Giving these external parties access within the application makes it vulnerable to cybercriminals who might gain access through their end. Moreover, if third-party services give data, it’s a wise option to first check the validity of the data before utilizing it.
8. Keep Security Simple
Contrary to popular belief, keeping the application’s security simple is a better option than having complex designs. Complex systems are hard to correct when an error occurs. Troubleshooting can be time-consuming which would put the application at more risk.
This situation is an opportunity that cybercriminals can take advantage of. If programmers opt to create simple but effective security controls, the risk of errors can be significantly reduced.
Conclusion
Cybercriminals often lurk around websites that have poor security measures. Oftentimes, these poor security measures were mere results of failing to adhere to security by design principles – something that programmers should not take for granted.
For companies like Panera Bread, it was a failure to act upon a security warning. While securing your application can be taxing, it’s best to protect yourself from potential risks that might cost your millions of dollars.
If you’re looking to protect your company from transaction money laundering, then visit https://www.kychub.com/transaction-monitoring for more information. KYC hub offers an excellent transaction monitoring service that stops money laundering by recognising suspicious transactions. Protect your business today and invest in the latest technology.
TechnologyHQ is a platform about business insights, tech, 4IR, digital transformation, AI, Blockchain, Cybersecurity, and social media for businesses.
We manage social media groups with more than 200,000 members with almost 100% engagement.